November 17, 2025
Struggling with CI/CD Security? Here’s How Advanced DevSecOps Fixes It Fast

By Shyam Kapdi
Improwised Technologies Pvt. Ltd.
The world of building software keeps changing fast, so teams now move quicker thanks to tools that automate testing and launching - yet moving faster opens doors to tricky cyber dangers at each step, whether someone’s writing code or pushing updates live.
Protecting CI/CD pipelines isn’t just smart - it’s essential for keeping sensitive info, client details, and legal standards safe. Here, we look at a practical yet powerful method for integrating security into DevOps, helping teams boost protection fast while still moving quickly.
A security-focused CI/CD process isn’t just about meeting rules - it’s how you stay in business. A single flaw in your system might taint countless updates, leak user info, and quietly spread to connected networks.
Also Read: Why CI Isn’t Just for DevOps—A Developer’s Secret to Fewer Midnight Firefights
What is DevSecOps? Modern Definitions And Impact
DevSecOps means building safety steps right into how teams create software these days. By shifting protection earlier, tests that check for risks or rules run automatically throughout development - not just at the end. Rather than waiting till deployment, issues get caught each time new code is added or updated. This way, apps ship quickly without sacrificing defense.
CIs and CDs stop bad code from spreading, cut down on expensive fixes later, while helping meet new rules that keep changing. By baking safety steps right into build pipelines, DevSecOps makes this smoother - linking coders, tech crews, and security folks who used to work apart.
It is not simply scanning code earlier. It’s about:
- Standardizing security as software
- Automating all non-negotiable guardrails
- Embedding threat awareness into developer decisions
- Eliminating manual review cycles that slow product velocity
Building a Secure CI/CD Pipeline: Step-by-Step Framework
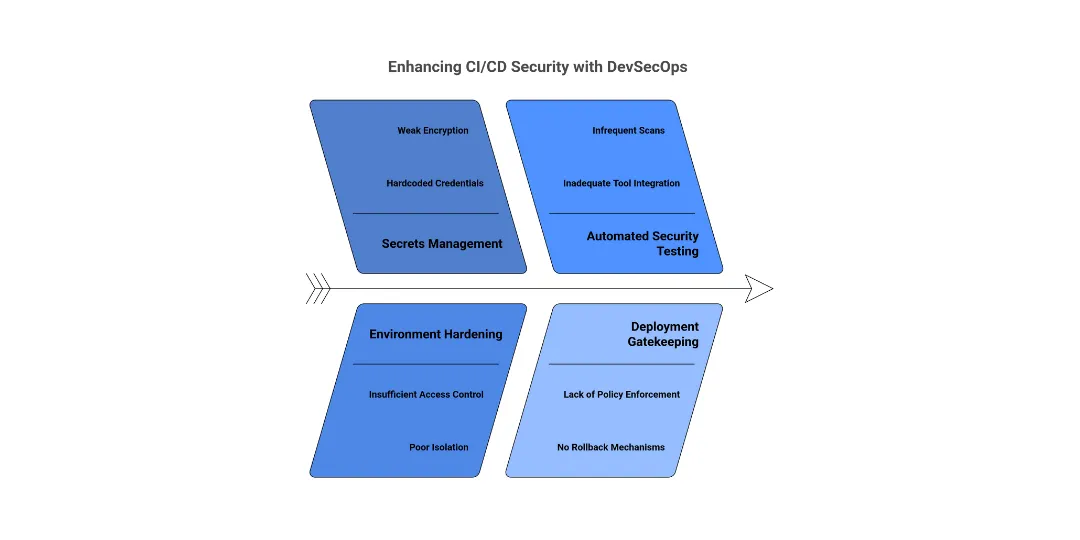
Creating a secure pipeline requires an end-to-end approach that integrates security controls from code commit to deployment.
-
Secrets Management: Use vaults and strong encryption to handle API keys, tokens, and credentials securely, avoiding hardcoding in source code.
-
Environment Hardening: Enforce strict role-based access control (RBAC), implement isolated build and deployment environments, and apply hardened configurations to reduce attack surface.
-
Automated Security Testing: Integrate SAST, DAST, SCA, and IAST tools to scan code and dependencies for vulnerabilities continuously.
-
Deployment Gatekeeping: Automate policy enforcement, approval workflows, and automated rollback mechanisms to catch risks in pre-production.
Also Read: CI/CD in Air-Gapped Environments: Running Pipelines Without Internet Access
Key Security Tools & Strategies for DevSecOps Integration
The modern DevSecOps toolbox is diverse, balancing open-source agility with enterprise-grade governance:
-
SAST (Static Application Security Testing) tools analyze source code early for risks such as injection flaws or insecure coding patterns.
-
DAST (Dynamic Application Security Testing) tools simulate attacks on running applications to identify runtime vulnerabilities.
-
SCA (Software Composition Analysis) tools detect known vulnerabilities in third-party libraries and containers.
-
IAST (Interactive Application Security Testing) tools combine static and dynamic analysis to pinpoint vulnerabilities during functional testing.
Open-source options get frequent upgrades plus real user feedback, yet often need solid setup skills. Big-name providers give unified views, audit-ready reports while handling heavy workloads smoothly. Picking the right fit means matching tool strengths to how complex your workflow is, what rules you follow, along your team’s know-how.
Shift-Left Security: Embedding Safety Early
Security early on means catching problems before they hit the main code or go live. It uses tools that automatically spot flaws, teaches devs safe coding habits, and applies rules through scripts right before merging or launching.
Examples show firms using early testing catch errors sooner - cutting live issues by a lot.
Take automated pre-merge SAST checks - they spot key flaws like BOLA fast, so teams avoid costly patching later because issues get caught sooner.
Cloud-Native CI/CD Threats and Resilience
Cloud-native architectures introduce specific security challenges in CI/CD pipelines:
- Containers and serverless functions are frequently updated and ephemeral, demanding continuous vulnerability scanning of base images and dependencies.
- Microservices create complex, distributed attack surfaces requiring automated policy-as-code enforcement and runtime admission controls.
- Cloud platforms themselves introduce risks through misconfigurations and over-permissioned roles; automation must restrict and monitor access dynamically.
Resilience is enhanced through hardened container registries, the use of policy engines like Open Policy Agent (OPA), and the segregation of duties across environments.
Continuous Pentesting and Runtime Protection
In rapid CI/CD, traditional pentesting is not enough. Continuous validation of security controls and exposure is ensured by including automated pentesting bots in development sprints.
By dynamically detecting and blocking exploit attempts in production, Runtime Application Self-Protection (RASP) technologies offer real-time monitoring and defence at the application layer. A layered defence that goes beyond static security checks is achieved by combining these strategies.
Developer-Friendly Security Feedback and Reporting
To reduce alert fatigue and friction, security tools must provide developers with prioritised, actionable insights that are integrated into their workflow. Developers can focus on crucial fixes without sacrificing speed by directly integrating security findings with contextual metadata and severity ratings into issue trackers.
A mature DevSecOps setup:
- Converts findings into ranked, business-impact-aware issues
- Auto-suppresses duplicates and noise
- Integrates directly with Jira, Linear, or GitHub Issues
- Generates remediation suggestions in developer language
Supply Chain Security & SBOM Automation
Managing supply chain risks is essential as open-source components take centre stage in software stacks. Real-time component provenance validation and vulnerability identification before deployment are made possible by automated Software Bill of Materials (SBOM) generation and reconciliation.
In order to prevent supply chain attacks that might compromise production systems by compromising dependencies or building objects, this proactive approach becomes crucial.
Modern SBOM automation includes:
- SBOM creation on every build
- Continuous reconciliation (not one-time generation)
- Real-time vulnerability mapping
- Sigstore attestation for provenance validation
Exception Handling and False Positive Management
A major obstacle in pipeline security is finding a balance between agility and robust enforcement. To reduce developer disruptions while maintaining security controls, advanced pipelines include automated false-positive suppression, risk-priority algorithms, and exception management workflows.
To stop risk creep, secure exceptions are recorded in audit trails and examined regularly.
Create a governance model where:
- Developers justify exceptions
- Security approves or auto-approves via policy
- All exceptions have expiry dates
- Risk is quantified, not guessed
Compliance, Audit, and Governance in CI/CD
Compliance is within CI/CD pipelines, and code automatically enforces security policies that are in line with laws like GDPR, SOC 2, and ISO. Pipelines simplify audits and lower human error by producing comprehensive policy enforcement reports and permanent logs.
While maintaining a constant regulatory posture, automated governance removes the overhead associated with manual compliance.
Integrate:
- Policy-as-code engines (OPA, Kyverno, Conftest)
- Audit logs for each pipeline stage
- Automated evidence collection for SOC2, GDPR, ISO27001
Autonomous CI/CD Pipelines: AI/ML Use Cases
Autonomous CI/CD pipelines that proactively identify unusual patterns in infrastructure configurations, runtime telemetry, and code changes are being driven by AI and machine learning. Before exploits happen, predictive analytics detects developing attack vectors, optimizes testing selection, and suggests remediations.
These developments indicate a time when security will constantly change without human intervention.
Use cases:
- Predictive vulnerability discovery
- Automated prioritization based on exploit likelihood
- AI-assisted secure code generation
- Anomaly detection across pipeline logs
- Self-healing pipelines (rerouting failures)
Organizing for DevSecOps: Culture, Process, and Team Change
The success of DevSecOps is not solely dependent on technical solutions. By encouraging shared accountability, integrating security champions into development teams, and coordinating disparate tooling ecosystems, organisations can overcome cultural barriers.
What works:
- A federated model where security engineers embed into product teams
- “Security office hours” for developer coaching
- Shared KPIs: delivery velocity + security health
- Reducing the mental tax of security by providing guardrails, not roadblocks
Real-Time Threat Intelligence Integration
Pipelines can dynamically modify security policies in response to new attacker tactics and vulnerabilities by integrating real-time threat intelligence platforms. By integrating global feeds and using automated alerts and mitigation triggers, continuous monitoring improves adaptive defences.
Integrate TI platforms directly into your pipelines:
- Auto-block malicious IPs
- Flag suspicious dependencies
- Detect emerging zero-days before your scanners do
- Feed signals back into SCA/SAST engines
Advanced API Security in CI/CD
APIs are critical yet vulnerable components in modern architectures. Securing APIs through DevSecOps involves continuous posture assessments, automated scanning for common threats like Broken Object Level Authorization, injection flaws, and enforcing API governance policies throughout development and production phases.
Also Read: Automate Kubernetes CI/CD Pipelines: Best Tools and Practices
Incident Response, Recovery, and Continuous Improvement
DevSecOps pipelines integrate automated mitigation workflows and continuous monitoring with incident response playbooks. Rapid damage control, paired with root cause analysis and feedback loops, drives continuous improvement and hardens pipelines against repeat threats.
Include:
- Automated containment workflows
- Rapid artifact revocation
- Build replay capability for forensic validation
- Post-incident learning loops feeding back into pipelines
Common Pitfalls and Remediation Strategies
Most organizations struggle with secrets sprawl, insufficient environment isolation, and alert fatigue. Successful remediation involves automated secrets vaulting, segregated environments, tailored alerting mechanisms, and continuous training.
- Giving CI runners admin/privileged roles
- Not signing artifacts
- No isolation between pipeline stages
- Assuming a “trusted build environment” without validation
- Security teams controlling tools that developers never use
Conclusion: Next Steps Toward Bulletproof CI/CD Security
Organisations must integrate AI/ML-assisted security intelligence, adopt shift-left practices, operationalise end-to-end automation, and promote cultural change to advance DevSecOps maturity. Teams can produce secure, agile software at scale by applying community-driven best practices, automated compliance, and strategic toolkits.


By Shyam Kapdi
Improwised Technologies Pvt. Ltd.


By Shyam Kapdi
Improwised Technologies Pvt. Ltd.


By Shyam Kapdi
Improwised Technologies Pvt. Ltd.
Optimize Your Cloud. Cut Costs. Accelerate Performance.
Struggling with slow deployments and rising cloud costs?
Our tailored platform engineering solutions enhance efficiency, boost speed, and reduce expenses.
